Ò»¡¢×éÍøÐèÇó
±£»¤×ܲ¿Óë·ÖÖ§×ÓÍøÖ®¼äµÄIPÊý¾ÝͨÐÅ£¬Í¨¹ýËíµÀ½¨Á¢Á¬½Ó£¬²¢¶ÔÊý¾Ý½øÐмÓÃÜ£¬±£Ö¤°²È«£¬GRE ovre IPSEC µÄÔÀíÊÇÓû§ÒµÎñÊý¾Ý·â±Õµ½GREËíµÀ£¬GREËíµÀµÄÊý¾ÝÔÙ±»ipsec¼ÓÃÜ£¬ËùÒÔÅäÖÃipsec¸ÐÐËȤÁ÷ʱ£¬Ô´µØÖ·ºÍÄ¿±êµØַΪÁ½¶Ë·ÓÉÆ÷µÄÍâÍø½Ó¿ÚµÄIPµØÖ·£»
¶þ¡¢×éÍøÍØÆË
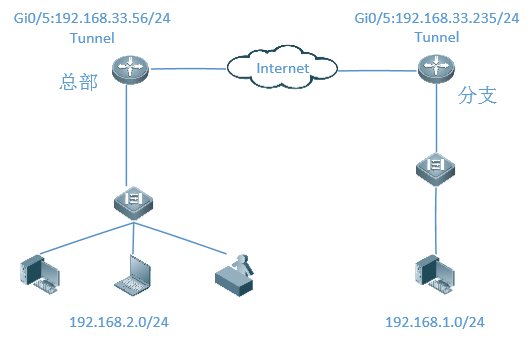
Èý¡¢¹¦ÄÜÔÀí
²ÉÓÃGRE½¨Á¢ËíµÀ£¬ÊµÏÖÄÚÍø¼äµÄͨÐÅ£¬Ê¹ÓÃipsec¶Ô×ܲ¿Óë·ÖÖ§¼äµÄËíµÀÁ÷Á¿½øÐмÓÃÜ
ËÄ¡¢ÅäÖÃÒªµã
1¡¢±¾ÅäÖÃÊǽ¨Á¢ÔÚEGÒѾÕýÈ·Íê³ÉÁË¿ìËÙÅäÖõĻù´¡Ö®Éϵģ»
2¡¢ÅäÖÃrouteA£¨×ܲ¿£©ÎªGRE
over ipsec·þÎñÆ÷¶Ë£»
3¡¢ÅäÖÃrouteB£¨·ÖÖ§£©ÎªGRE
over ipsec¿Í»§¶Ë£»
4¡¢Á½¶ËµÄ²ÎÊýÒª±£³ÖÒ»ÖÂ
GRE TunnelµÄËíµÀµÄÔ´Ä¿µÄµØÖ·ÒªÏ໥¶ÔÓ¦
ÈÏÖ¤·½Ê½£ºÔ¤¹²ÏíÃÜÔ¿£¬ÃÜԿΪruijie
IKEËã·¨£º3DES-MD5£¬DH2
IPSecÐÉ̽»»¥·½°¸£ºesp(3des-md5)
Îå¡¢ÅäÖò½Öè
WebÉÏ»¹²»Ö§³ÖGREËíµÀµÄÅäÖã¬Ö»ÄÜÔÚCLIÏÂÅäÖÃ
1.×ܲ¿
1)¡¢ÅäÖÃipsecµÚÒ»½×¶Î
crypto isakmp enable
crypto isakmp policy 1
encryption 3des
authentication pre-share
hash md5
group 2
2)¡¢ÅäÖÃÔ¤¹²ÏíÃÜÔ¿ºÍ±ä»»¼¯ºÏ
crypto isakmp key 0 ruijie
address 192.168.33.235
crypto ipsec transform-set
myset esp-3des esp-md5-hmac
mode transport
3)¡¢ÅäÖøÐÐËÁ÷
ip access-list extended 199
10 permit gre host 192.168.33.56 host
192.168.33.235
4)¡¢¶¨ÒåÒ»¸ö¼ÓÃÜÓ³É伯ºÏ
crypto map mymap 1
ipsec-isakmp
set peer 192.168.33.235
set transform-set myset
match address 199
5)¡¢ÔÚ½Ó¿ÚÉϵ÷ÓüÓÃÜͼ
interface GigabitEthernet
0/5
ip address 192.168.33.56
255.255.255.0
crypto map mymap
6)¡¢ÅäÖÃGREµÄTunnel½Ó¿Ú
interface tunnel 1
tunnel source 192.168.33.56
tunnel destination 192.168.33.235
ip address 2.2.2.1
255.255.255.0
7)¡¢ÅäÖ÷ÓÉ
ip route 192.168.1.0 255.255.255.0 tunnel 1
ip route 0.0.0.0 0.0.0.0
192.168.33.1
#192.168.33.1ΪÍâÍøÍø¹Ø
2.·ÖÖ§
1)¡¢ÅäÖÃipsecµÚÒ»½×¶Î
crypto isakmp policy 1
encryption 3des
authentication pre-share
hash md5
group 2
2)¡¢ÅäÖÃÔ¤¹²ÏíÃÜÔ¿ºÍ±ä»»¼¯ºÏ
crypto isakmp key 0 ruijie
address 192.168.33.56
crypto ipsec transform-set
myset esp-3des esp-md5-hmac
mode transport
3)¡¢ÅäÖøÐÐËÁ÷
ip access-list extended 199
10 permit gre host 192.168.33.235 host
192.168.33.56
4)¡¢¶¨Òå¼ÓÃÜÓ³Éä
crypto map mymap 1
ipsec-isakmp
set peer 192.168.33.56
set transform-set myset
match address 199
5)¡¢ÔÚ½Ó¿ÚÉϵ÷ÓüÓÃÜͼ
interface GigabitEthernet
0/5
ip address 192.168.33.235
255.255.255.0
crypto map mymap
6)¡¢ÅäÖÃGREµÄTunnel½Ó¿Ú
interface tunnel 1
tunnel source 192.168.33.235
tunnel destination
192.168.33.56
ip address 2.2.2.2
255.255.255.0
7)¡¢ÅäÖ÷ÓÉ
ip route 192.168.2.0 255.255.255.0 tunnel 1
ip route 0.0.0.0 0.0.0.0
192.168.33.1
#192.168.33.1ΪÍâÍøÍø¹Ø
Áù¡¢ÅäÖÃÑéÖ¤
1.²é¿´ipsec״̬
zongbu#show crypto state
destination
source
state
st-id pa-st mapid mode
ir lifetime
192.168.33.235 192.168.33.56 IKE_IDLE
1 0 1 9 1 85948
2.²é¿´ËíµÀÁ÷Á¿
zongbu#show
crypto ipsec sa
Interface:
Tunnel 1
Profile
map tag:profile-map
==================================
sub_map type:profile, seqno:0, id=1
local ident (addr/mask/prot/port):
(192.168.33.56/0.0.0.0/47/0))
remote ident (addr/mask/prot/port):
(192.168.33.235/0.0.0.0/47/0))
PERMIT
#pkts
encaps: 4861, #pkts encrypt: 4861, #pkts digest 4861
#pkts
decaps: 0, #pkts decrypt: 0, #pkts verify 0
#send
errors 235, #recv errors 0
Inbound esp sas:
spi:0x34ef2301 (888087297)
transform: esp-3des esp-md5-hmac
in use settings={Transport Encaps,}
crypto map profile-map 0
sa timing: remaining key lifetime (k/sec): (4606445/3143)
IV size: 0 bytes
Replay detection support:Y
Outbound esp sas:
spi:0x10c2d27a (281203322)
transform: esp-3des esp-md5-hmac
in use settings={Transport Encaps,}
crypto
map profile-map 0
sa timing: remaining key lifetime (k/sec): (4606445/3143)
IV size: 0 bytes
Replay detection support:Y